strong password
What is a strong password?
A strong password is one that is designed to be hard for a person or program to guess. Because the purpose of a password is to ensure that only authorized users can access resources, a password that is easy to guess is a cybersecurity risk.
When people create login credentials, they often defeat the purpose by creating a memorable password. They choose their names, phone numbers, birthdays or even the word "password" itself, the most commonly used password for many years.
Now that many password policies require the inclusion of a numeral, the most common password is "password1."
Instead, the best way to prevent a data breach, identify theft or other unauthorized access to private information, is to create complex, long passwords.

What is considered a strong password?
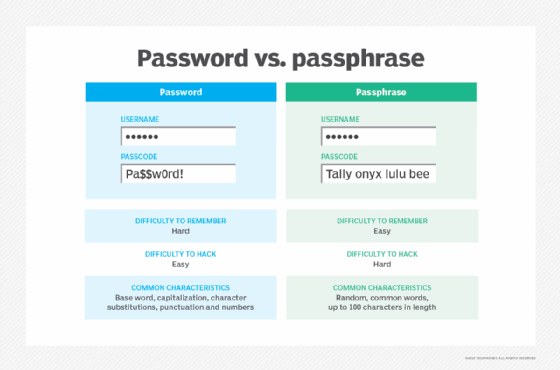
Instead of common words that are easy to guess, essential components of a secure password include sufficient length and a mix of special characters, numbers, and uppercase and lowercase letters.
People like to use passwords that will be easy for them to remember, so an easy way to create a new password that is both secure and easy to remember is to use a common passphrase and convert that phrase to a password.
So a password example might be, "I have 2 Labrador retrievers! Fido and Spot," which could be expressed as Ih2Lr!F+S.
How do passwords get stolen?
There are a few ways passwords and other sensitive data can be stolen, but phishing and brute force attacks are the two most common ways.
Phishing scams
Phishing is the process whereby cybercriminals use intimidation, fear or tricks through social engineering to get a user to reveal their password or sensitive information to them.
For example, a criminal could pose as a representative of a person's credit card account, telling them that there's been an unlawful charge to the account. Then they ask you to log in via a link to a fake version of the bank website to verify the charges.
Once they submit the victim's login credentials, they intercept the data.
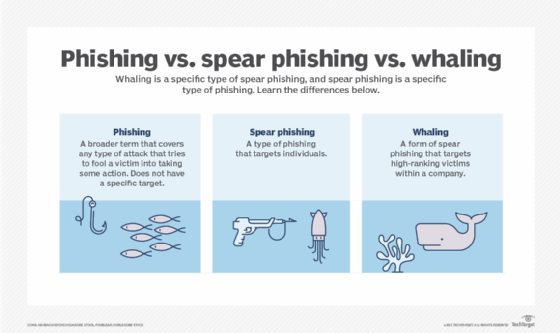
Brute force attack
With a brute force attack, a hacker might try to manually guess your account or use a password cracker to try combinations of the password until they reach the correct one.
A six-character, single-case password has 308 million possible combinations, all substitutions of which a password cracker can go through in just a few minutes.
However, combining uppercase letters and lowercase letters and using eight characters instead of six increases the possible combinations to 53 trillion; substituting a number for one of the letters yields 218 trillion possibilities, and substituting a special character or punctuation for another yields 6,095 trillion possible combinations.
Although a password cracker can eventually go through that many combinations, it requires much more time and computing power for hackers to break a more complex password. For organizations, this extra time can be vital to preventing a data breach.
Additional tips for better online security
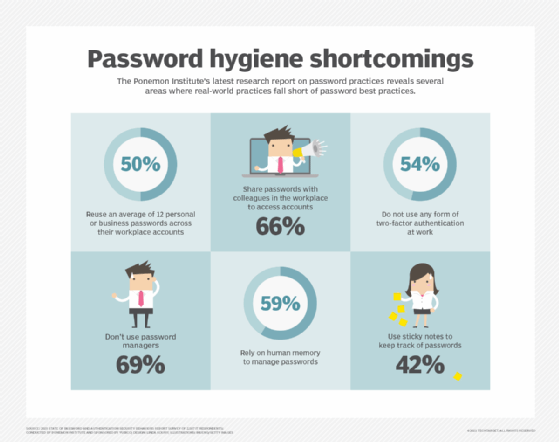
While it may seem like a burden to create a strong password for every account, there are some ways to make it easier and create an added layer of security at the same time.
Use a password manager
If creating and remembering complex passwords sounds too challenging to do or enforce with employees, consider a password manager application.
These apps come with a unique password generator that will create (and store) complex, longer passwords for each application or website.
These are also commonly referred to as single sign-on (SSO) applications as they require the user to only sign in with a master password. The application will auto-login the user when they visit one of their pre-programmed sites.
This relieves the burden of the user having to remember numerous passwords while adding to your security. These password manager apps can be used for any site that requires a password, including social media websites, work tools and email carriers.
Many operating systems such as Microsoft Windows and iOS come with complementary password managers. However, there are third-party SSO applications as well. Examples include LastPass, Dashlane and NordPass.
Use multifactor authentication
Another way to enhance security is through two-factor authentication, or multifactor authentication, which employs an additional login measure before granting users access to a site or online account.
While this isn't enough, on its own, to replace a weak password, it does add another level of security to a strong password.
Typically, this is an application downloaded to a mobile phone where the user can submit login credentials or use a biometric device, like a thumbprint.
Use a VPN
When connecting to the internet via a public Wi-Fi source through your mobile device or laptop, it's easy for hackers to use the same Wi-Fi network to intercept private data transmitted over the network.
A great way to avoid this is with a virtual private network (VPN), which creates an encrypted network connection. Users can leverage a VPN to give themselves more privacy online or to bypass geographic-based censorship.
Employ antivirus software
While antivirus software won't necessarily help users fortify their password, it can help you shore up their other cybersecurity defenses.
If a threat actor can hack into your account or system, a good antivirus program will be able to detect it and stop it.
Learn more about how to prevent password attacks and other exploits and top cybersecurity best practices to protect your business.







