enterprise mobility management (EMM)
What is enterprise mobility management (EMM)?
Enterprise mobility management (EMM) software allows organizations to securely enable employee use of mobile devices and applications.
In addition to addressing security concerns, EMM software helps employees be more productive because IT departments can provide them with the applications and data they need to perform tasks on mobile devices. EMM software can also help organizations with bring your own device, or BYOD, environments to manage various device types.
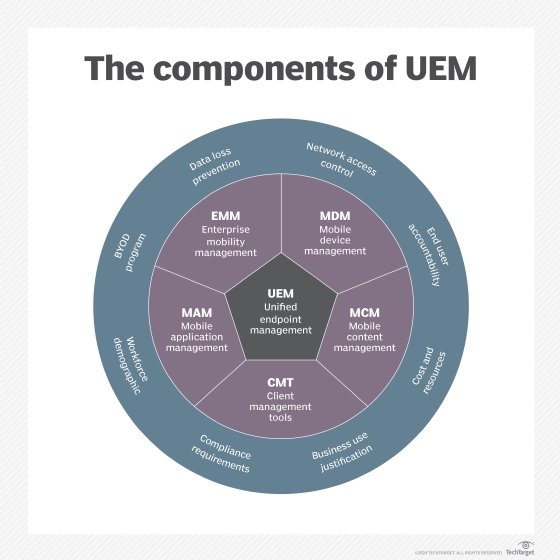
EMM grew out of mobile device management (MDM), which focused solely on device-level control and security. After Microsoft's 2015 release of Windows 10, most EMM software providers expanded into unified endpoint management (UEM), allowing IT to manage PCs and mobile devices through a single console.
Components of EMM
EMM typically involves some combination of MDM, mobile application management (MAM), mobile content management (MCM) and identity and access management (IAM).
- MDM. Mobile device management is the foundation of any enterprise mobility suite. It relies on the combination of an agent app installed on an endpoint device and server software running in the corporate data center or the cloud. Administrators use the MDM server's management console to set policies and configure settings. The agent enforces these policies and configures these settings by integrating with application program interfaces (APIs) built into mobile operating systems.
- MAM. Mobile application management provides more granular management and security. It enables admins to set policies for a specific app or subset of apps rather than the whole device. Some apps have specific MAM APIs built in, while others rely on the device-level MAM APIs in most major mobile OSes.
- MCM. Mobile content management enables IT to control which applications may access or transmit corporate data.
- IAM. Identity and access management features control how, when and where workers may use corporate apps and data, while offering some user-friendly features, such as single sign-on. Many EMM vendors incorporate identity features like federation and multi-factor authentication.
These four technologies started as individual products but are increasingly available through broader UEM platforms.
Benefits of EMM
EMM is a powerful tool businesses can use to manage their mobile devices and applications. It helps control costs, improve security, reduce potential user and device downtime and maximize productivity. For example, if an employee's device is lost or stolen, IT admins can use EMM to locate or remotely wipe and reset a device to ensure data security. Additionally, EMMs allow IT admins to distribute applications remotely to end-user devices to ensure they can access all necessary data. This helps to ensure that employees are more productive and that corporate information is managed and secure. EMM benefits can include the following:
- Increased device security. EMM tools provide powerful security features, such as data encryption and remote wiping capabilities, to help protect corporate devices and data.
- Improved productivity. With EMM, organizations can ensure that employees have access to the resources they need, when they need them, to remain productive throughout their day. These resources include applications, access to the network and service set identifier settings, bookmarks and more.
- Streamlined IT management. Administrators can use EMM platforms to manage device configurations remotely and quickly, reducing time spent managing individual devices. In addition, IT teams can manage all mobile devices from a single interface instead of using multiple tools or manual processes for each device type. This makes deploying new applications, managing user profiles and enforcing security policies much easier.
- Lower costs. Using an EMM tool, organizations can reduce operational costs by automating many IT management tasks like manual device provisioning, adding features like device tracking and locating, and providing access to advanced reporting and metrics to help troubleshoot and secure devices.
- Improved user experience. With tools like automated device enrollment -- also called zero-touch -- IT can give employees streamlined setup processes with easy access to the resources they need while using their devices.
- Improved security and reduced risk of data loss. EMM tools help organizations secure their data by deploying policies to ensure that only authorized users can access sensitive information.
- Improved compliance. With an EMM platform, organizations can more easily meet their regulatory compliance requirements by better understanding what mobile devices are on the network, how they are being used, and features and capabilities to lock and reset devices.
Challenges of EMM
While there are many benefits to implementing an EMM, there are challenges organizations face that should also be considered when looking to choose and deploy an EMM platform, including the following:
- Learning curve of new technologies. The biggest challenge when implementing an EMM platform is the learning curve. Depending on the size, complexity and sophistication of the organization's IT environment, it can take some time for IT administrators to learn these new skill sets, become familiar with EMM features and understand how they interact with existing systems.
- Cost of implementation. EMM platforms can be expensive to implement and maintain, which can be a significant challenge for companies with limited budgets. In addition, companies also need to consider the cost of training or hiring additional staff to support the technology.
- Compatibility. Companies must ensure their chosen EMM is compatible with existing infrastructure and software to avoid costly implementation issues. While it is common for companies to have more than one EMM, that increases the complexity of an environment. When considering EMM platforms, consider which operating systems are supported, as well as compatibility with other areas like the company directory platform, identity provider integration and any third-party integrations the company may use.
- Integration. Integrating existing enterprise applications and third-party tools with a new EMM tool can be complicated, requiring close coordination between IT teams and developers. This can take considerable time and effort to accomplish correctly.
- Support. Organizations may need external support for their EMM provider, depending on what issues or problems arise. This could increase overall costs and cause delays in resolving issues, depending on the support services included with the chosen EMM platform and provider. Many vendors and service providers offer additional deployment and support services. Companies can also look at mobility managed service providers, which offer a completely managed experience for a company's EMM and mobile help desk.
- Employee user acceptance and onboarding. User acceptance of EMM tools can be challenging because users may have concerns over new restrictions and security settings on their devices. Additionally, suppose a company has hundreds or thousands of employees who need access to new managed devices. In that case, it can be difficult to quickly get them up and running without disrupting workflow or leaving gaps in support coverage. Therefore, companies must ensure that all users fully understand the importance and benefits of using an EMM system, in addition to developing EMM policies and providing training and support as end users start enrolling devices.
These are just some of the challenges associated with EMM tools that organizations should consider when evaluating potential options for their mobility needs. However, these challenges can be successfully addressed and overcome with the proper implementation and management strategy. By clearly understanding what the organization needs from an EMM tool and properly training users on how to use it, companies can ensure they get the most out of their investment.
How EMM has evolved
As more organizations embraced enterprise mobility, vendors started creating what would become EMM by adding MAM or MCM features to their MDM products. An enterprise app store or other self-service portal for application delivery and deployment is also a common component of EMM software.
Microsoft built MDM APIs into Windows 10, which opened the door for EMM software to manage PCs in the same way it manages smartphones and tablets. Apple also allows its macOS desktops and laptops to be managed this way. Now that all major EMM vendors support this functionality, the market has shifted from EMM to UEM, which can manage a variety of endpoints, including internet of things devices, wearables and tablets.
Today, most EMM vendors have rebranded into UEM vendors. Vendors like Microsoft and VMware also incorporate UEM components into digital workspace offerings. Digital workspaces aim to unify the end-user experience even further by bringing applications, virtual desktops, mobile devices and more onto one platform.