SMTP (Simple Mail Transfer Protocol)
What is SMTP (Simple Mail Transfer Protocol)?
SMTP (Simple Mail Transfer Protocol) is a TCP/IP protocol used in sending and receiving email. SMTP is used most commonly by email clients, including Gmail, Outlook, Apple Mail and Yahoo Mail.
SMTP can send and receive email, but email clients typically use a program with SMTP for sending email. Because SMTP is limited in its ability to queue messages at the receiving end, it's usually used with either Post Office Protocol 3 (POP3) or Internet Message Access Protocol (IMAP), which lets the user save messages in a server mailbox and download them periodically from a server. SMTP is typically limited to and relied on to send messages from a sender to a recipient.
What is an SMTP server?
An SMTP server is an application or computer that sends, receives and relays email. These servers typically use TCP on port 25 or 587. The port number identifies specific processes when an internet or network message is forwarded to a server. All network-connected devices come equipped with standardized ports that have an assigned number. Each number is reserved for certain protocols and their associated functions.
SMTP servers are set to an always-on listening mode and as soon as a server detects a TCP connection from a client, the SMTP process initiates a connection to port 25 to send the email.
Outgoing SMTP servers send messages for users. Email clients which are used to read and send emails, must also have the Internet Protocol (IP) address of the SMTP server. To handle issues such as spam, server administrators must control which clients can use the server. They can do this either by restricting users by their IP address or, more likely, by imposing a system or command that requires the authentication of clients.
How SMTP works
SMTP uses a client-server model as follows:
- An email server uses SMTP to send a message from an email client to another email server.
- The email server uses SMTP as a relay service to send the email to the receiving email server.
- The receiving email server uses an email client to download incoming mail via IMAP, for example, and places it in the recipient's inbox.
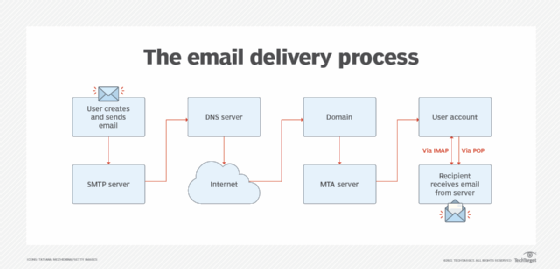
So, for example, when a user clicks the "send" button, a TCP connection is established that links to an SMTP server. When the SMTP server receives the TCP connection from a client, the SMTP process starts a connection through port 25 to send the email.
From here, the SMTP client tells the server what to do with information such as the sender's and recipient's email addresses and the email's content. A mail transfer agent (MTA) then checks if both email addresses are from the same email domain. If they're from the same domain, the email is sent; if not, the server uses the domain name system (DNS) to identify the recipient's domain and then sends it to the correct server.
The recipient then uses IMAP or POP3 protocols to receive the email.
Commands in SMTP are issued automatically without the need for the end user to enter them. As an example, the HELO command is the email client identifying itself to a server. Other SMTP commands include the following:
- MAIL. This command is used to initiate a message transfer. This tells the SMTP server that a new transaction is starting.
- RCPT. This command follows MAIL. It identifies the replicant email address.
- DATA. This command starts the transfer of data between the client and server. Message contents are moved to the SMTP server.
- QUIT. Once the email is sent, the client sends this command to the server to cease the connection.
- RSET. This command is used to abort the mail transaction. The command is sent to the server, where all data about the email is removed.
SMTP vs. IMAP and POP
Hosted on an SMTP server, SMTP is used to send, relay or forward messages from a mail client and isn't used to receive messages; IMAP and POP are used instead.
IMAP is a standard email retrieval protocol that manages and retrieves email messages. It keeps an email on a server and then synchronizes it across different devices. IMAP enables users to organize messages into folders, flag messages and save draft messages on the server. Users can also have multiple email client applications that sync with the email server to consistently show which messages are read or unread.
IMAP functions as the intermediary between the email server and email client. When users read an email using IMAP, they read them off the server. They don't download or store the email on their local device.
Most email servers and clients support POP and use it to receive emails from remote servers and send them to a local client. POP is a one-way client-server protocol in which emails are received and held on the email server. POP also enables users to download emails from a server to the client so the recipient can view the email offline.
When used together, SMTP and either IMAP or POP transmit email messages.
While POP is considered a store-and-forward service, IMAP is thought of as a remote file server, because the user can store the email on the server and access it from any device or location as needed.
POP and IMAP are supported by modern email clients and web servers. But unlike POP, IMAP also synchronizes emails across multiple devices or clients.
SMTP vs. ESMT
Extended Simple Mail Transfer Protocol (ESMTP) is an extension to the original SMTP for sending emails that support graphics, audio and video files, as well as text in various languages. ESMTP was released in 1995 for users who wanted to attach multimedia files to emails. The updated protocol enabled newer functions like protecting servers while saving bandwidth. Most commercial email servers and clients support ESMTP.
Unlike in ESMTP, multimedia files can't be directly attached to an email in SMTP without the help of Multipurpose Internet Mail Extensions (MIMEs). Likewise, ESMTP enables users to reduce the size of emails, while SMTP doesn't.
SMTP vs. HTTP APIs
SMTP has been used since 1982 and remains the most common email protocol to send an email message. However, there has been a trend toward using cloud-based Hypertext Transfer Protocol (HTTP) application programming interfaces (APIs) to send and receive email.
HTTP APIs offer two advantages: First, the communication between email client and server -- for example, when using mobile apps -- is faster than SMTP because HTTP APIs require fewer back-and-forth commands to authenticate the sender and recipient. Second, APIs offer functionality that isn't available using SMTP.
SMTP and Unix-based systems
On Unix-based systems, Sendmail remains the most widely used SMTP mail server for email. Sendmail provides behind-the-scenes email transport and is typically used with a separate user-friendly interface.
SMTP usually is implemented to operate over internet port 25. An alternative to SMTP that's widely used in Europe is X.400/X.500. When it was created, X.400 was intended to serve as the primary international protocol. Among most users, X.400/X.500 has been eclipsed by SMTP, but it remains popular in the defense and telecommunications industries.
In-house SMTP servers vs. third-party services
SMTP servers can be set up in-house or as a third-party service. In-house SMTP servers run independently, while a provider runs third-party SMTP servers.
Third-party SMTP vendors take care of everything from maintenance and monitoring of email servers to security. This means users don't need the expertise or budget to run and maintain their own in-house server. However, users still must be concerned about downtime caused by outages or any additional terms and conditions.
In-house SMTP servers aren't limited to only sending a specific number of emails per day, as some third-party providers may do. However, users must have the technical knowledge and money to maintain, run and monitor the server. Additionally, users are responsible for implementing their own security. This could include selecting secure email protocols, keeping server firmware up to date, or using email server firewalls.
SMTP vendors
Examples of SMTP service providers include the following:
- Amazon SES. Amazon Simple Email Service (SES) is an add-on to AWS. It's a cloud-based SMTP service that enables marketers and developers to send marketing, notification and transaction email campaigns. SES, however, doesn't track and monitor message events.
- SendGrid. This cloud-based SMTP email service offers high scalability along with email analytics, delivery optimization tools, email templates and integration with other apps.
- Sendinblue. This SMTP service supports transactional emails, email marketing, SMS and live chat. It also supports third-party applications such as Google Analytics and Salesforce platforms.
- SendLayer. This transactional SMTP service offers email analytics, email tracking and an email list management system.
Pricing models differ by vendor, as some offer a monthly price for a specific number of emails users can send, while other vendors offer paid plans per month or pay-as-you-go models. Free versions of each SMTP tool might also be available but are normally limited by the number of emails users can send.
Learn more about SMTP and its functions, along with 11 other common network protocols.
