More Details on KB4056892 Wintel Vulnerabilities
As I mentioned in a 1/5 blog post, major vulnerabilities for Intel and Amd processors emerged over the holidays. KB4056892 addresses them, at least in part. But running the Get-SpeculationControlSetting PowerShell script (available within the PS window for download) is disturbing. It shows that on most machines a firmware/BIOS update from the PC or motherboard vendor is also required to patch these vulnerabilities. Among the more details on KB4056892 Wintel vulnerabilities I provide here is unwelcome news that few such updates are available. In fact, many hardware vendors haven’t released such updates, particularly for older systems. Let me elaborate…
Here Are More Details on KB4056892 Wintel Vulnerabilities
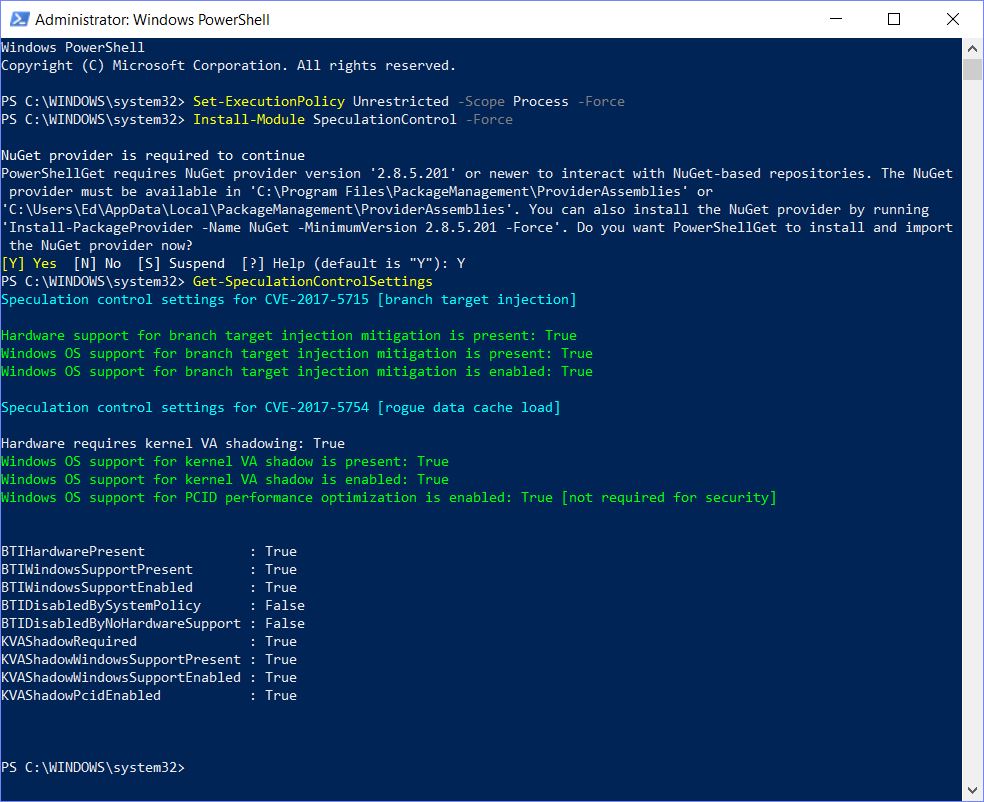
Right now, my only fully-patched system is my Surface Pro 3. It is fully patched because MS released the firmware updates at the same time they let go of related Windows OS and application updates on 1/3. None of my other systems currently qualifies, even though the newest ones are only 12 to 24 months old. To illustrate a complete patch, output from the PowerShell script on the Surface Pro 3 is quite revealing, on a variety of topics:
PS Script output for fully-patched Surface Pro 3.
[Please click image for full-sized view.]
Here’s what this output tells me:
1. It shows the sequence of activities necessary to run the Get-SpeculationControlSetting script, which include obtaining and installing the NuGet package provider to handle its installation.
2. It names the two vulnerabilities involved: branch target injection (BTI), and kernel VA shadow (KVAS). It also identifies their IDs in Mitre’s Common Vulnerabilities and Exposures (CVE) database — namely CVE-2017-5715 and CVE-2017-5754, respectively.
3. It shows that for BTI, that both hardware and Windows OS support are present, thanks to KB4056892 and a same-day firmware update for the Surface Pro 3.
4. The Windows OS is patched for KVAS (2nd group of green lines).
What About Systems Missing HW Support for BTI?
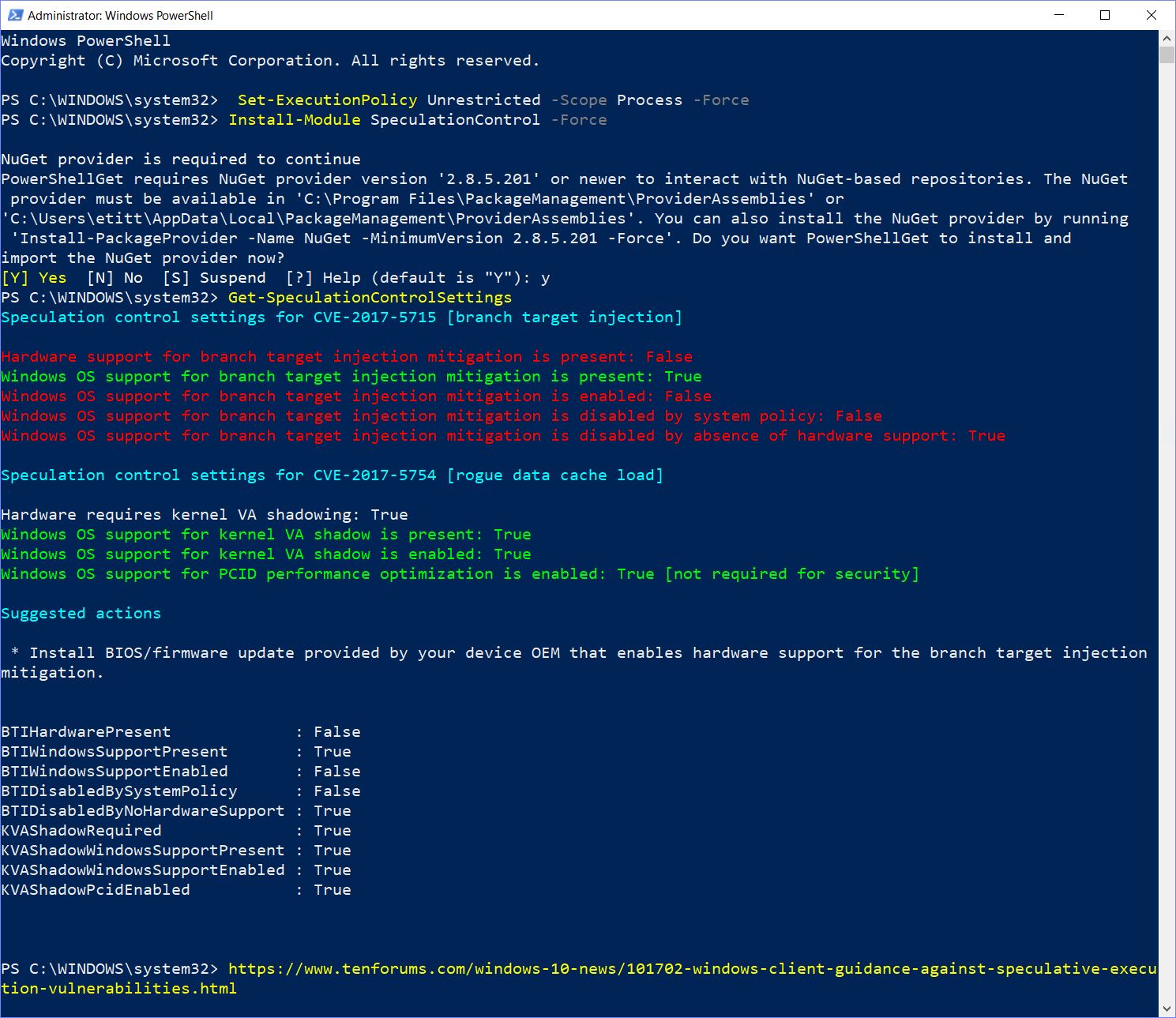
Alas, the 7 remaining systems here at Chez Tittel all produce the same depressing (or scary) results. I show the PS script output for my production desktop, built in January 2016 from 2015 parts. It tells a different story:
PS Script output for partly-patched homebrew desktop with Asrock Extreme7+ mobo, i7-6700, etc.
[Please click image for full-sized view.]
As the red lines in that output indicate, a few things are missing. Here’s what it says, in a form parallel to the preceding screen capture:
1. Same sequence of activities to make Get-SpeculationControlSetting script work.
2. Same recitation of vulnerability info.
3. Alas, no hardware support for BTI means Windows OS support is disabled.
4. Indeed, KB4056892 addresses the KVAS vulnerability.
Hopefully, I don’t have to explain why I’m checking the Asrock, Dell and Lenovo sites daily for updates to affected systems’ firmware. If your PCs are in the same boat, you should probably be doing the same. I’ll be patching those systems as soon as updates appear, and you should do likewise for yours.
[Note Added 1/12/18 9 AM]
Last night, when I ran Dell Update on my Venue Pro 11, I found a BIOS update for that machine. In the meantime, I’ve not only updated my BIOS to version A22 (dated 1/2, released 1/10), I’ve also upgraded that machine to the latest Insider Preview (Build 17074.1000). Happily, despite a couple of scares, the BIOS update didn’t brick the Dell unit — as reported for other Dell PCs recently — and the OS upgrade installed successfully, too. A quick run of the Get-SpeculationControl PS script shows all-green status for both vulnerabilities now, too. One more Dell, two more Asrock mobo PCs, and two more Lenovo laptops to go! Stay tuned…
[NOTE Added 1/16/18 9:40 AM]
Aryeh Goretsky of ESET created, and is maintaining, a database of all vendors with Meltdown/Spectre responses on the record. There are currently 210 entries in this list (which includes links to their info and responses) as I write this note. This is absolutely, positively the BEST and MOST COMPREHENSIVE coverage of the vendor responses that I’ve found or seen so far. Check it out: “Meltdown and Spectre CPU Vulnerabilities: What You Need to Know.” I’m blown away by the time and effort that went into putting this together…]
[NOTE Added 1/17/18 9 AM]
ComputerWorld Editor extraordinaire Val Potter touts Steve Gibson’s utility named InSpectre (get it?) that puts an approachable face on the Get-SpeculationControlSettings PS script. If you want your users (or friends, family, and other hangers-on) to do their own Spectre/Meltdown checks, this little tool will make it much easier for them to run the check and to interpret the results. To wit: