What is BitLocker?
BitLocker is a Microsoft Windows security and encryption feature included with certain Windows versions. BitLocker enables users to encrypt everything on the drive Windows is installed on, protecting that data from theft or unauthorized access.
Microsoft BitLocker improves file and system protections by mitigating unauthorized data access. It uses the Advanced Encryption Standard algorithm with 128- or 256-bit keys. BitLocker combines the on-disk encryption process and special key management techniques.
Although BitLocker first debuted with Windows Vista in 2006, beginning with Windows 10 version 1511, Microsoft updated BitLocker, introducing new encryption algorithms, expanded Group Policy settings, and enhanced functionality for operating system (OS) drives and removable data drives. This update applies to Windows 10 and 11, as well as Server 2016, 2019, 2022 and 2025. BitLocker works on Windows Pro, Enterprise and Education editions.
How does BitLocker work?
BitLocker uses a specialized chip called a Trusted Platform Module (TPM), which stores Rivest-Shamir-Adleman encryption keys specific to the host system for hardware authentication. The original computer manufacturer installs the TPM, which works with BitLocker to protect user data.
In addition to using a TPM, BitLocker can lock the startup process until the user inputs a personal identification number (PIN) or inserts a removable device, like a flash drive with a startup key. BitLocker also creates a recovery key for the user's hard drive in case they forget or lose their password.
Computers without a TPM installed can still use BitLocker to encrypt Windows OS drives. However, this implementation requires a USB startup key to turn on the computer or resume from hibernation mode. Microsoft states there's more prestartup system integrity verification when BitLocker is paired with a TPM.
BitLocker Recovery Password Viewer and BitLocker Drive Encryption tools are additional tools for managing BitLocker. BitLocker Recovery Password Viewer enables users to locate BitLocker recovery passwords backed up to Active Directory (AD) Domain Services. This tool is used to recover data stored on an already encrypted drive. BitLocker drive encryption tools combine command-line tools, the BitLocker cmdlets for Windows PowerShell, and manage-bde and repair-bde. Repair-bde, for example, is used in disaster recovery attempts where BitLocker-protected drives can't be unlocked normally or using the recovery console. The manage-bde command-line tool turns BitLocker on or off. Turning off BitLocker decrypts all the files on the drive when that data no longer needs protection.
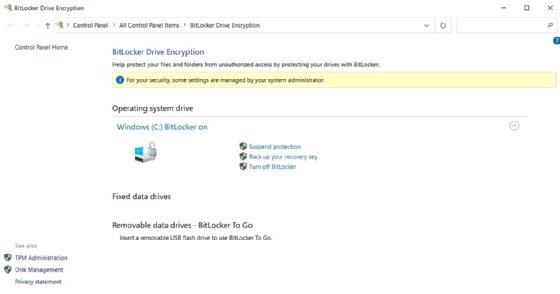
How to use BitLocker
BitLocker is enabled by default. But, if it's turned off, a user can go to the Windows search bar and search for Manage BitLocker. If BitLocker is on the device, it shows up in Control Panel, with one of the options being to Turn on BitLocker. Other options include Suspend protection, Back up your recovery key and Turn off BitLocker.
Users can perform various other functions, including encrypting BitLocker, recovering from a BitLocker lockdown, and configuring and disabling BitLocker.
Encrypting BitLocker
After turning on BitLocker, Windows begins checking system settings. The user must create a password they use whenever they access their PC or drive.
The user then selects Recovery key settings. After clicking on Next, they can choose how much of their drive they wish to encrypt. The two volume encryption options are to encrypt used disk space only or the entire drive. Encrypt used disk space refers to only the disk space that contains data, while Encrypt the entire drive means that the entire storage volume, including free space, is encrypted.
The user can run a BitLocker system check to ensure the tool can access the recovery and encryption keys before anything is encrypted.
After the system check, BitLocker Drive Encryption Wizard restarts the computer to begin the endpoint encryption process. Protection is only enabled after the user signs on and the device is registered to an AD domain.
Recovering from a BitLocker lockdown
When an unauthorized user attempts to use a device, BitLocker locks it down. However, an authorized user can unlock the device using their unique 48-digit numerical BitLocker recovery key, which is usually stored in the user's Microsoft account.
If the recovery key is lost, the user must reinstall Windows. To avoid this, BitLocker recovery keys can be accessed from the following locations:
- The user's Microsoft account. Users can view their key if they sign in to their Microsoft account on another device.
- USB flash drive. A USB flash drive can store the key, which can be inserted into the locked PC to unlock it. If the key is stored as a text file, the user can plug it into another PC to read the password.
- The user's Microsoft Entra ID account. The key might be stored in a larger Entra ID account associated with the user's device.
- A system administrator's system. A sys admin might have the recovery key if the user's device is connected to a domain.
- The user's possession. The user could have printed out or written the code on paper.
Configuring BitLocker
Advanced users or IT can configure BitLocker. The purpose of manually configuring BitLocker, instead of allowing it to be activated and operate with its default settings, is to tailor it to the organization's specific security encryption requirements for a particular device and user. The following steps for custom-configuring BitLocker are much the same as what a user would use:
- Click on Settings > System > Storage.
- Click on Advance Storage settings > Disk volumes.
- Select the drive with the partitions to encrypt using the Properties button.
- Click on the Turn on BitLocker option.
- Save the BitLocker recovery key to the appropriate Microsoft account.
- Specify the parameters of BitLocker encryption, such as Encrypt used disk space only, and run a final BitLocker system check.
Disabling BitLocker
BitLocker can be disabled using Manage BitLocker, which is located in the Windows search bar. Select the option to Turn off BitLocker, and once the user confirms, the data decryption process begins.
Features of BitLocker
BitLocker can be used on portable media, such as USB devices, as well as on laptops, desktops and smartphones.
The BitLocker security authentication routine requires users to verify their identities before the OS launches. Unauthorized parties can't gain access to files without the proper identification password, key or PIN.
BitLocker integrates with AD, where recovery keys can be stored and managed across a network. With BitLocker keys safely stored in AD, network administrators can deploy, manage and recover BitLocker devices.
BitLocker automatically encrypts all drives on compatible devices, saving users from doing it themselves. However, there are still ways to encrypt all or a partial set of files on older and semicompatible devices.
Use cases for BitLocker
Millions of mobile and laptop devices are lost, stolen or misplaced each year by remote workers, field office employees and others who work or travel away from the office. With BitLocker, the data residing on a lost or misplaced device is encrypted, making it difficult for bad actors to access.
Key use cases for BitLocker include the following:
- Helps with regulatory compliance. Companies can improve compliance with regulatory requirements, such as Health Insurance Portability and Accountability, International Organization for Standardization, National Institute of Standards and Technology, and System and Organization Controls 2. BitLocker doesn't cover every regulatory requirement, but it helps attain compliance with the encryption that it provides.
- Secures company-owned devices. BitLocker helps prevent insider security breaches since only the employees directly assigned to a device are authorized to access the encrypted content.
- Protects data on old computers. BitLocker ensures that the data on decommissioned devices, such as computers, remains inaccessible to unauthorized users.
BitLocker system requirements
BitLocker has the following requirements:
- TPM 1.2 or later must be installed. Otherwise, a startup key must be stored on a removable device.
- If using a TPM, a Trusted Computing Group-compliant BIOS or Unified Extensible Firmware Interface (UEFI) is needed for a chain of trust for the OS startup.
- The system BIOS or UEFI must support the USB mass storage device class.
- Storage drives must have two or more partitions.
- For system drives using the BIOS firmware, the OS drive must be formatted with New Technology File System.
- System drives that use UEFI-based firmware must be formatted with the File Allocation Table 32 file system.
Limitations of BitLocker
Although BitLocker can help safeguard data from unauthorized access, it also has the following limitations:
- Requires a TPM chip for best use. To obtain maximum functionality from BitLocker, the device must have a TPM chip. Although the device can still be used without a TPM chip, it requires the assistance of a USB startup key, which doesn't provide the same level of integrity verification.
- Requires a BitLocker recovery key. Users might not be aware of the need for this key and could inadvertently delete it when cleaning up files. The key can also be lost if the user's device experiences a hardware failure.
- Has limited BitLocker security protection. BitLocker only protects the contents of the device on which it's installed. While it can protect data and applications that physically reside on the device, it's ineffective against outside threats, such as malware, that enter from the internet or a network.
- Can experience performance impacts from encryption. The encryption that BitLocker enables can slow down machine performance.
Employees and employers must share the responsibility for enterprise security hygiene. Learn what best practices can help both groups secure corporate assets.







