Target network
This excerpt from Chapter 2 of "Protect Your Windows Network from Perimeter to Data," by Jesper Johansson and Steve Riley, is about.securing networks by understanding how hackers take advantage of your mistakes.
 |
The following excerpt is from Chapter 2 of "Protect Your Windows Network from Perimeter to Data" written by Jesper Johansson and Steve Riley. Click for the complete book excerpt series or purchase the book. |
|
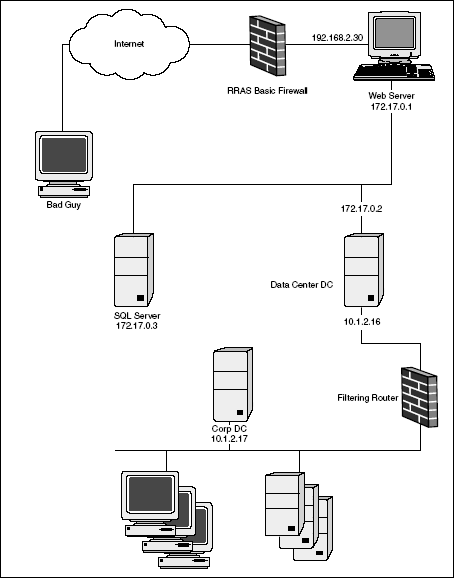
Target Network Before we start attacking our target network, let's take a look at what we are up against. Obviously, a real attacker going after a real network would only rarely have access to network diagrams; in our case, however, it is enlightening to look at the configuration of the target network, such as the one shown in Figure 2-1. Our target network is a standard dual-screened subnet with a firewall at the front and a filtering router at the back. The perimeter network (also known as DMZ, demilitarized zone, or screened subnet) has a pretty common setup with a front-end Web server, a back-end database server, and a DMZ domain controller (DC). There is a corporate DC on the back end. The end goal is to take over that DC.
Perhaps the only unusual aspect to this network is the fact that the Web server and the Data Center Domain Controller (DC) are both serving as routers. This is actually an artifact of how this demonstration was constructed. The network was built as virtual machines running in Microsoft Virtual PC 2004. This is to make the network portable enough to run on a single laptop. Had we built this with separate routers, we would have needed three laptops (or two more than we want to carry). To that end, the Web server and Data Center (or DMZ) DC are both serving as routers to reduce the number of host machines needed. However, this somewhat unorthodox configuration has no bearing on what is to come. Click for the next excerpt in this series: Network footprinting Click for the book excerpt series or visit Addison-Wesley to purchase the book. |