Put your Windows 10 deployments on AutoPilot
Aaron Parker talks cloud management, MDM, and provisioning for Windows 10.
Windows desktop deployments are hard—enterprise deployments have typically required creating custom SOEs, application packaging, infrastructure to support Windows deploy, plus testing and piloting. Then of course, managing those PCs once deployed.
Microsoft is seeking to simplify PC management with Windows 10, using Azure AD and Mobile Device Management. I'm seeing lots of interest in this because it provides a cloud-only approach to PC deployment and management. Typically, this comes from organizations deploying new infrastructure, migrating to Office 365, or even some long term ConfigMgr shops looking to simplify desktop management.
However, this does come with caveats, and it requires some explanation for anyone new to the concept. Is it for everyone? Well, let's look at what Windows 10 mobility management means and what the implications are for the management of desktops
Microsoft has included MDM capabilities in Windows since Windows 8.0, and has improved them with 8.1 and further still with Windows 10. Each subsequent major release has added to this functionality and along with Intune, Microsoft has been turning MDM into a viable approach for managing PCs.
An admission here—I'm very Microsoft focused, so when I think of MDM solutions, I'm generally thinking in terms of Microsoft Intune's capabilities. However, 3rd party MDM solutions have been touting their Windows 10 management capabilities, too.
Building for the cloud
So, if you're interested in a cloud-only approach to deploying Windows 10 PCs, what does it take? You'll need a few pieces:
Azure Active Directory
Windows 10 Modern Management is built around Azure Active Directory, requiring an organization to embrace Azure AD as a cloud identity solution. There's still a place for 3rd party identity products, but just as Microsoft did in the early 2000s with Active Directory, they're able to leverage email (i.e. Office 365) as the gateway into Azure AD as the primary identity service.
With a cloud-based identity and Windows 10, we have the ability to deploy Windows 10 devices to users without the need for on-premises identity solutions. And you can do this for free—Azure AD has multiple editions, include a free version. Most organizations, though, are going to pay for Azure AD in some form to gain additional features. This includes automatic MDM registration—Azure AD Premium is required, whether or not you're using a 3rd party MDM solution.
You can adopt Azure AD by synchronizing your existing on-premises Active Directory, or if you're looking at a greenfield deployment, perhaps go directly to Azure AD instead.
Mobile Device Management
MDM is of course the cornerstone of the cloud-only solution, so you'll need an MDM product capable of managing Windows 10. There's Intune, AirWatch, MobileIron, IBM MaaS360, and probably others. Some of these include agents you can deploy to PCs; however, this perhaps defeats the purpose of a cloud first approach.
Windows Store for Business
More applications delivered via the Windows Store means less time packaging and updating applications. The Windows Store for Business allows you to deliver modern applications to Windows 10 devices; however, it's also a way to remove in-box applications by targeting them for uninstall.
I highly recommend spending time to discover applications that can be delivered via the Windows Store and could replace legacy Win32 apps.
Optional Components
To protect corporate information on PCs that could be anywhere, use Windows Information Protection to classify data as personal or work allowing you to remove corporate data remotely.
Providing an enterprise file sync and share solution and email from the cloud (whether that be Office 365 or something else) ensures users’ data is available across all of their devices and provisioned on the fly.
Considerations
While I see a future for Windows 10 modern management, there are a few gotchas today that might hinder adoption of this approach in your environment:
Provisioning Devices
Users provision the PC - Need a new PC? Pick one up from the store and provision right out of the box. No need to pick up the phone and call IT.
Modern management enables you to get out of the SOE business. Windows 10 PCs instead use the OS as installed by the OEM, and then the user does the work of provisioning a device (rather than IT). That's no different from MDM-managed phones, but of course, a Windows PC is a little more complex.
Hardware
Windows 10 PCs for modern management should also be carefully selected for enterprises, ensuring specific hardware requirements for things such as BitLocker. Windows 10 Pro is required at minimum, and devices can be upgraded to Enterprise over the wire.
Administrators
By default, users become an administrator on the machine they've just provisioned. This is similar to a mobile phone where users effectively have admin rights; however, unless you're running Windows 10 S or enable Device Guard, these PCs continue to be able to run untrusted code.
Applications
Application deployment for Windows 10 MDM is restricted to Windows Store apps and applications that can be installed via a single MSI file. That means no EXEs or MSIs with CAB files, etc.
Somewhat ironically today, I can't deploy the desktop version of Citrix Receiver to Windows 10 devices via an MDM solution. Citrix XenApp would be a great solution for delivering legacy applications, but there's a challenge deploying the client to access those apps. The Citrix Receiver UWP app is now available, which we could deploy; however, there are many reasons to deploy the full featured desktop version of Receiver.
Policies
Modern management does not provide the same level of control that IT is used to with AD domain-joined PCs. Depending on how you approach PC management, this might be an issue for you or it might not.
The number of MDM polices is increasing with each Windows 10 release and you can now deploy a subset of Group Policies via MDM. There are 3rd party solutions that can deploy traditional Group Policy to non-domain joined PCs, for example PolicyPak.
Data
Apart from applications, which you could engineer around for most cases, the biggest challenge in changing your approach to PC management and not joining those PCs to a traditional AD domain is data.
Users understand drive letters - changing to an EFSS solution might require some training or a change of workflows. Organizations have all sorts of existing data that may not even be suitable for access via an EFSS solution. Choose a solution that allows you to deliver from both on-premises and cloud-based storage.
Conditional Access
Modern management requires you to understand device compliance. First, you need to work out what a compliant device is and then the tools needed to implement compliance. Conditional Access then protects services from non-compliant devices.
Conditional Access requires applications to become aware of modern authentication. Ideally applications integrate with Azure AD via SAML authentication, otherwise some workarounds are required.
The Future with Windows AutoPilot
Windows 10 Fall Creators Update (1709) and Windows AutoPilot will improve the enrolment and provisioning process greatly.
Today, users become administrators on an Azure AD joined PC, and policies and applications deploy after the enrolment process is complete. AutoPilot allows IT to control whether users are administrators on their devices, customizes the out-of-box experience (OOBE), and serializes the enrolment process so that policies apply and apps install before the user logs on. IT can also pre-provision devices or control which devices can be enrolled as corporate devices.
Technically you can use AutoPilot today to customize the OOBE on Windows 10 1703, but these features are still in development, so we'll get a complete picture of how Windows AutoPilot will improve the deployment process after September.
Configuring Windows AutoPilot
If you have signed up for the Microsoft Store for Business, you might already have access to Windows AutoPilot—if not, you should be seeing this rollout soon. On the Devices link, the AutoPilot configuration is displayed. Today, AutoPilot is very simple—there are three components to configure:
- Devices: our target Windows 10 devices.
- Device Group: a simple way to group similar devices and target profiles.
- Profiles: configuration settings applied to the device during enrolment.
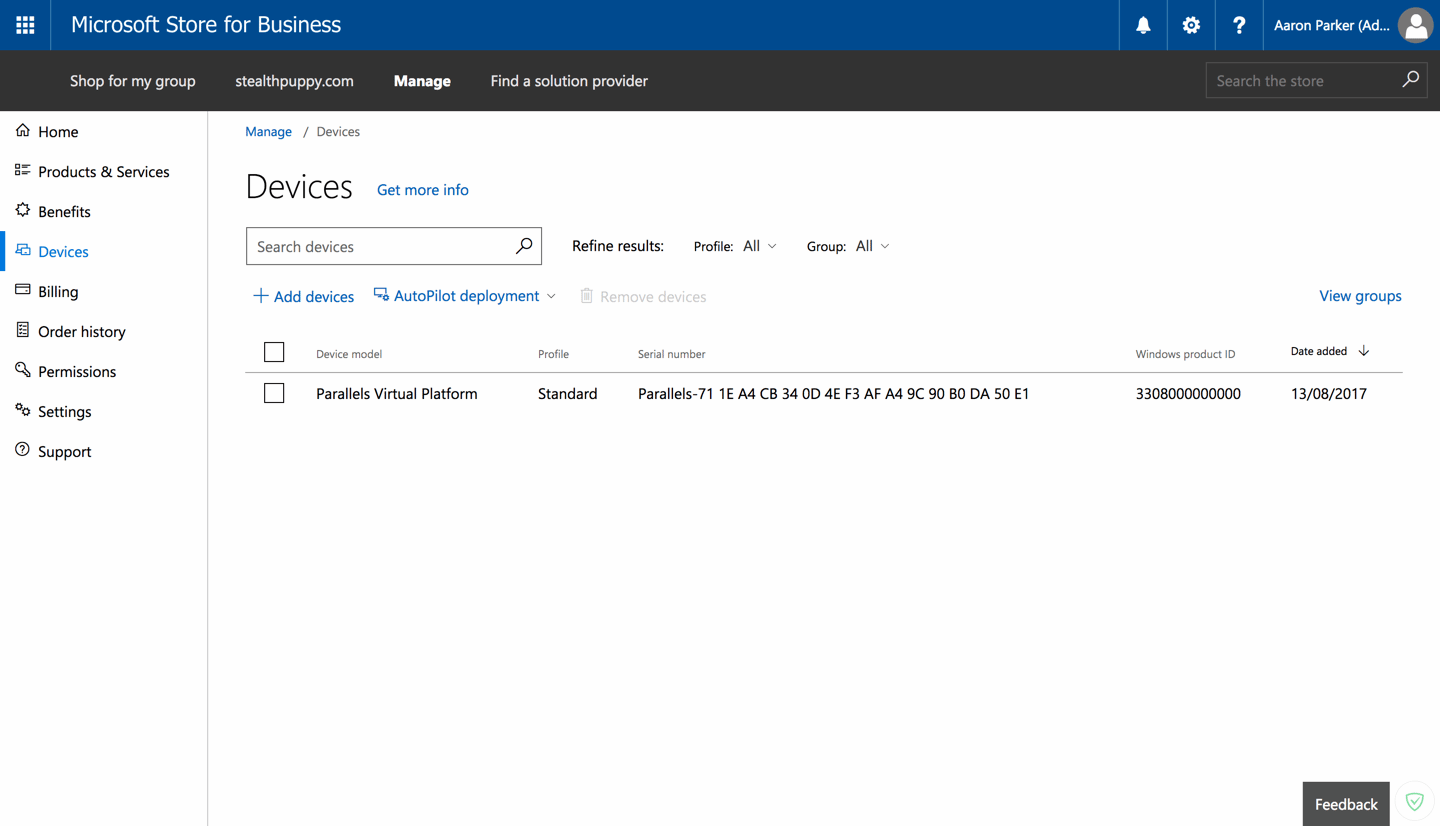
Here you can apply configurations to devices. Devices’ identifiers are either provided by the OEM when devices are shipped, or obtained by the IT administrator from existing machines via a PowerShell script.
Profiles define the configuration to apply to the device, which you then assign to devices or device groups. Right now, AutoPilot includes these settings:
- Skip Cortana, OneDrive, and OEM registration setup pages; Automatically setup for work or school; Sign in experience with company brand
- Skip privacy settings
- Disable local admin account creation on the device
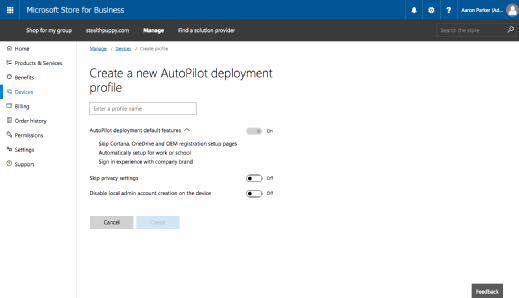
So, today AutoPilot is quite simple but I'd expect to see the improvements delivered alongside each new Windows 10 release.
Who Is This For?
Modern management isn’t something applied to all PCs. Knowledge workers with simple application requirements would be suitable, and they might access legacy applications via Citrix XenApp. In-house applications could be migrated to Universal applications or transformed using the Desktop Bridge to enable delivery via the Windows Store or MDM, allowing you to deliver just about any app.
Users and applications may be straight-forward to move to modern management for Windows 10; however, the biggest challenge will always be data, especially when users have a requirement to get to traditional on-premises data locations. If you're deploying greenfield it likely you won't have this challenge, but always consider how users need to get access to their data and let that define how PCs are to be managed.
Even so, I have seen the future - it's managing end-user devices with no on-premises infrastructure, and where the enterprise makes no restrictions on OS. One where devices are disposable, and are provisioned on the fly. A future where IT no longer manages an SOE or packages applications. And I can't wait.







